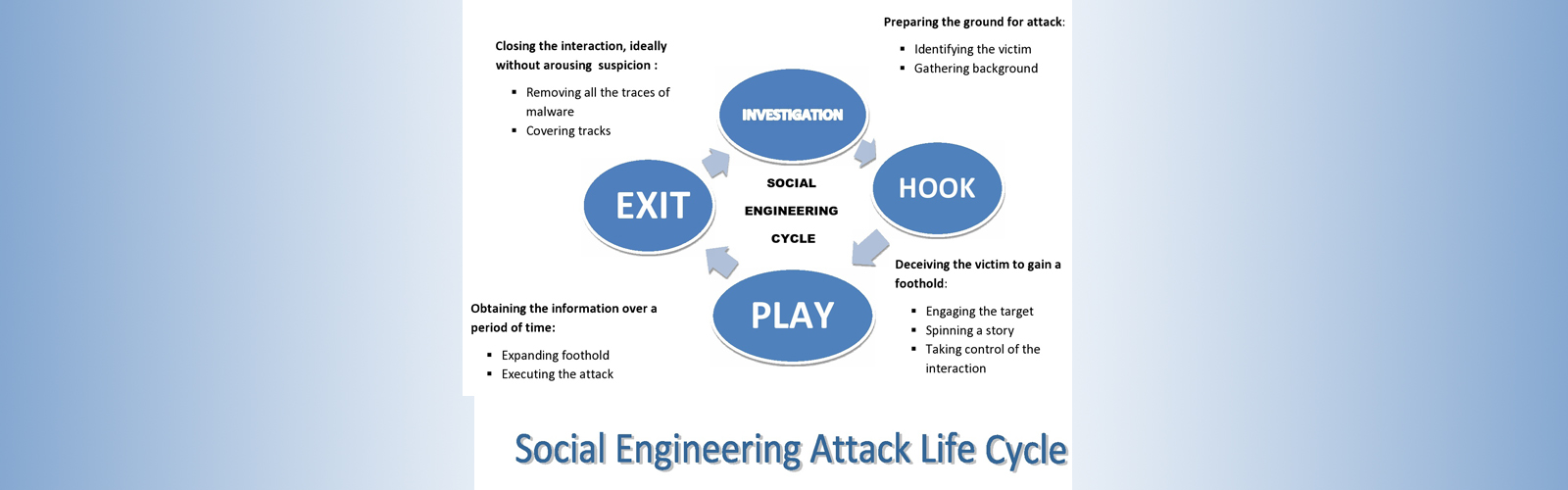
Attack Cycle
People easily got facilitate with some attractive things like beauty , profit etc shown over digital world which in actual is a trap. In the digital world it is necessary for every professional, businessman and student to see both positive and negative aspects of anything related to technology. So lets understand the attack cycle of social engineering.
- INVESTIGATION The very first phase of attack where attacker prepares the ground for attack. In this they will choose victim very smartly. Then there comes the role of information gathering process where they collect the maximum information about victim. In this process your social media platforms(Instagram, Facebook, Snapchat, LinkedIn etc) helps them telling a lot about you, your likes /dislikes, your professional background, even your nature.These information are enough for a good social engineer to hack you. After gaining the most of information, they choose the method of attack that could have more probability to be successful.
- HOOK The second phase is making connection with victim. They will approach victim with very friendly nature and by spinning a story they will try their best to target your emotions and winning your trust. The connection might be very small like helping someone at office door and letting them in, however connection might be a little long as hacker may become your online friend over instagram. It all depends what kind of attack hacker is doing and also the method which is adopted.
- PLAY After making the successful connection, hacker will execute the attack. Again depending upon the type of attack, execution will be in different form. Like after winning trust of victim they convinced him to click on some link that seems out be malicious later. Thus taking out your sensitive data, your money and more is done under this process. Or considering above example if you let someone into your company, he will collect all data of company with him.
- EXIT The hack is incomplete for any hacker without deleting all traces of his hack. They will delete all interaction done with victim. Covering each and every attack, they will remove all traces of malware and bringing the charade to normal. After this everything would seem like nothing had happened.